Blocking traffic from a single IP with AWS
A few days ago, https://gomore.dk was being hammered by traffic from some IP address in Dubai.
It looked like someone was running a scan with Acunetix and it was causing a 30x increase in traffic to some URLs. So obviously I wanted to block all traffic from that single IP, and after some digging in the AWS console, I found out how to do this.
So here is a quick tutorial.
1. Open your VPC dashboard
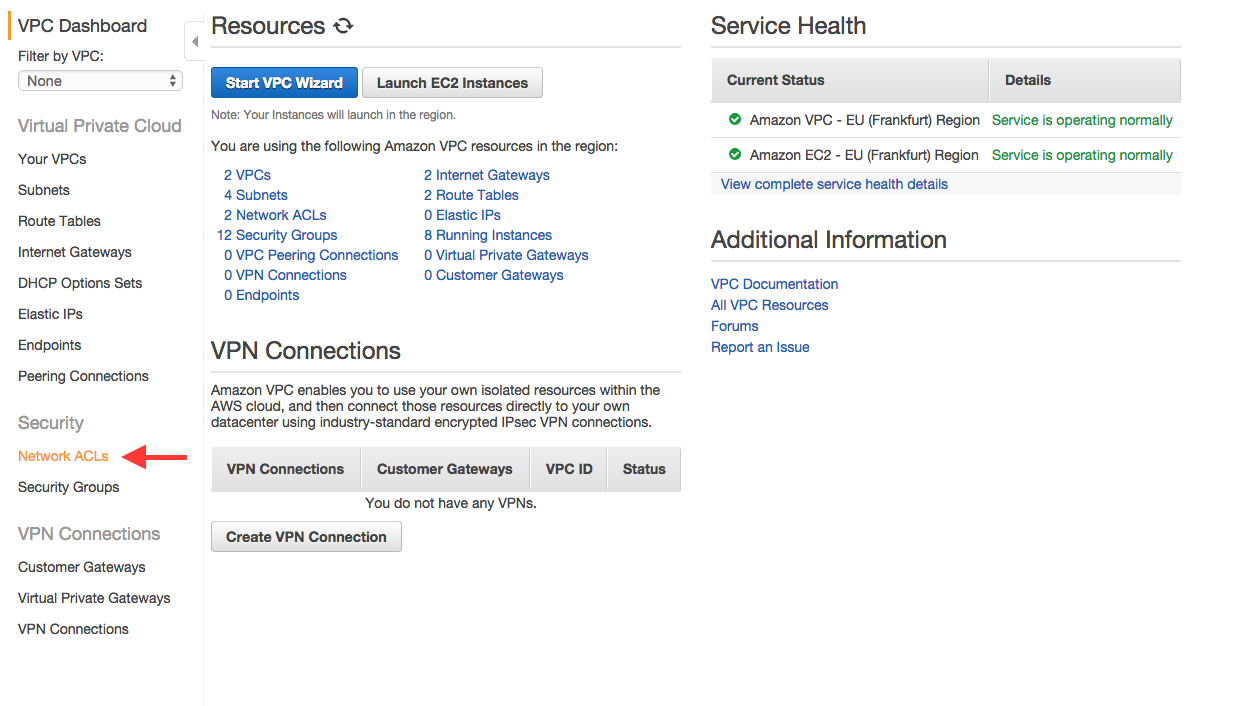
2. Open the “Network ACLs” view
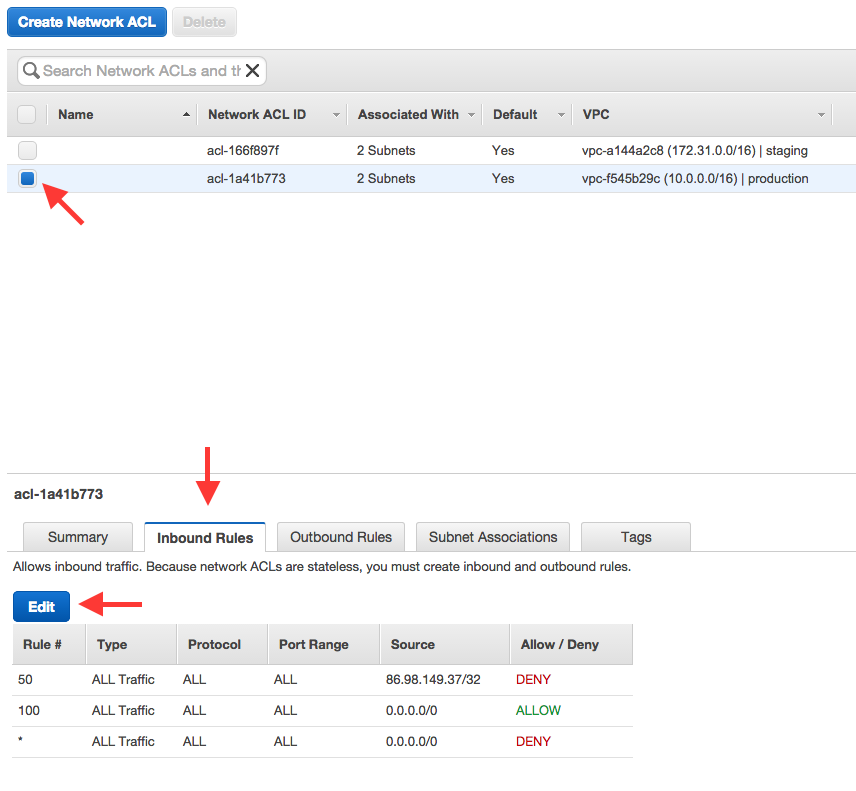
3. Open the ACL editor
- Select the subnet to which your EC2 instances or load balancers are connected.
- Click “Inbound Rules”
- Click “Edit”
4. Add a rule to block the traffic
You will now see the ACL editor. On the last row, you can add a new rule.
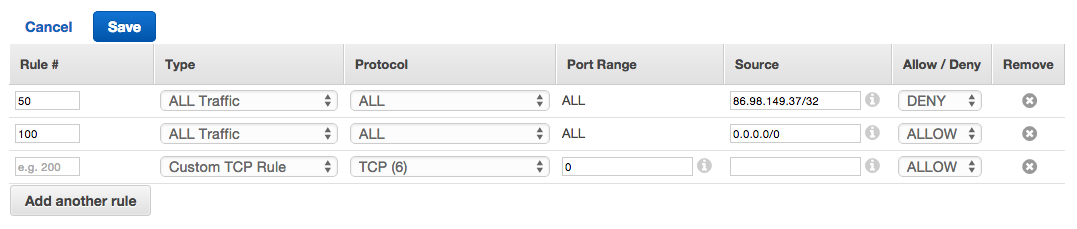
Here is how you should fill out the fields:
| Rule # | Use any number less than 100, which is the number of the default accept-all rule. This is important because rules are evaluated in order, and your rule needs to come before the default. |
| Type | Select “All traffic” |
| Protocol | Locked to “ALL” |
| Source | The CIDR you want to block. To match a single IP address, enter it here and append /32. For example, I blocked 86.98.149.37/32 |
| Allow/Deny | Select “DENY” |
Now click Save and you should see the updated rules table.
Note
While searching for a way to block traffic, I found lots of articles saying that it wasn’t possible because the security group rules in AWS only support whitelisting. So I think this level of control may be a relatively recent addition to AWS.